
intelligent monitoring solution combined with traditional monitoring systems

Intelligent monitoring solution combined with traditional monitoring systems. It uses AI technology to read the video streams from every camera 24/7, analyze and judge the behavior information of moving targets automatically, and output the information to related system platforms. It provides timely early warnings for potential safety incidents, which can greatly reduce the workload of monitoring personnel.
Yuxing Technology Video Monitoring Analysis System (HVS) Adopting advanced video analysis algorithms.

Hardware Adaptation Development
Some projects in mainland China cannot use foreign chips. Our team can adapt algorithms for specific hardware.

Remote Deployment Offline Use
Deployed in a large number of judicial projects over China. These projects have been running stably until now and cannot be connected to the external network.

Continuous Algorithm Optimization
The team continuously optimizes algorithm performance: reducing hardware configuration, improving algorithm performance, enhancing algorithm accuracy, and providing highly customized algorithms adapted to large models.
Absolute Price Advantage
Focused on providing the most cost-effective video monitoring analysis solutions.
The behavior recognition function is the core of the intelligent monitoring system. It uses artificial intelligence and deep learning technology to automatically analyze human actions and behavior patterns in surveillance video, thereby achieving real-time monitoring, abnormal pre-warning, and efficient management.
The system uses algorithms to structure the main activity skeleton of people. Various abnormal behaviors are defined based on human movement trajectories, and an action system is formed through deep learning algorithms, which can be efficiently recognized by the system.


Face recognition is one of the most focused and widely used functions in current intelligent monitoring systems. It pushes monitoring from the stage of "passive recording" to "active identity recognition." It is commonly used for security access and control, blacklist warning, and VIP customer identification.
The system uses a deep learning-based detection algorithm to find the location of all faces in the video stream, standardizes the faces through key point localization and geometric transformation, converts face image information into digital codes using a convolutional neural network, and finally compares it with templates stored in the database to achieve accurate face recognition.
The object/item recognition function utilizes AI to give the monitoring system the ability to "understand" the screen, enabling the monitoring system to transform from passive recording to active early warning, achieving efficient event response and intelligent retrieval. It greatly improves the efficiency and accuracy of security monitoring and is a core pillar of modern intelligent security.
The system is based on deep learning, inputting the video stream into a pre-trained AI model to accurately identify preset object categories (such as people, vehicles, etc.) and mark their precise locations on the screen. Based on their movement, stopping, or interaction in the screen, the system triggers preset intelligent events.

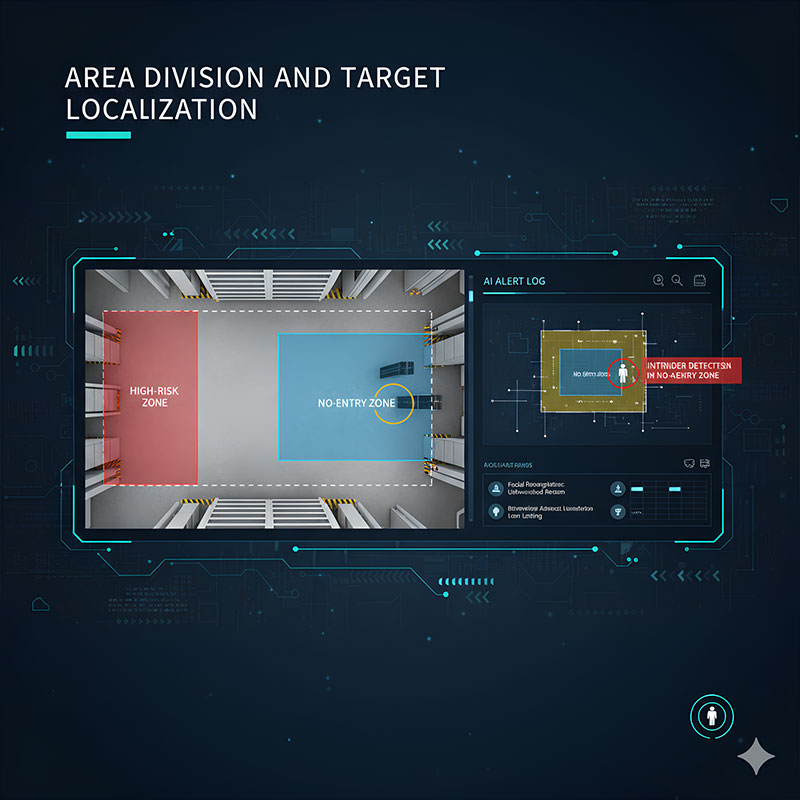
The system allows you to freely define areas of interest in any shape on the screen, based on your actual monitoring scenario (e.g., High-Risk Zone, Restricted Access Zone, Important Asset Storage Area). All recognition functions (such as behavior, facial, and object recognition) can be activated or excluded within these specific zones, significantly improving the accuracy and relevance of alarms. You can localize the focus area down to centimeter precision, ensuring the system only monitors the areas you truly need to protect.
The system not only provides preset recognition functions, but also utilizes Large Model Analytics to process user-defined, specialized recognition rules. This allows for personalized coverage in areas not addressed by the system's general recognition rules.
Simply use natural language (for example, 'A person in black clothing is pushing a wheelchair forward') to tell the system what you want to monitor, and the new recognition rule will take effect immediately, without the need for complex code.

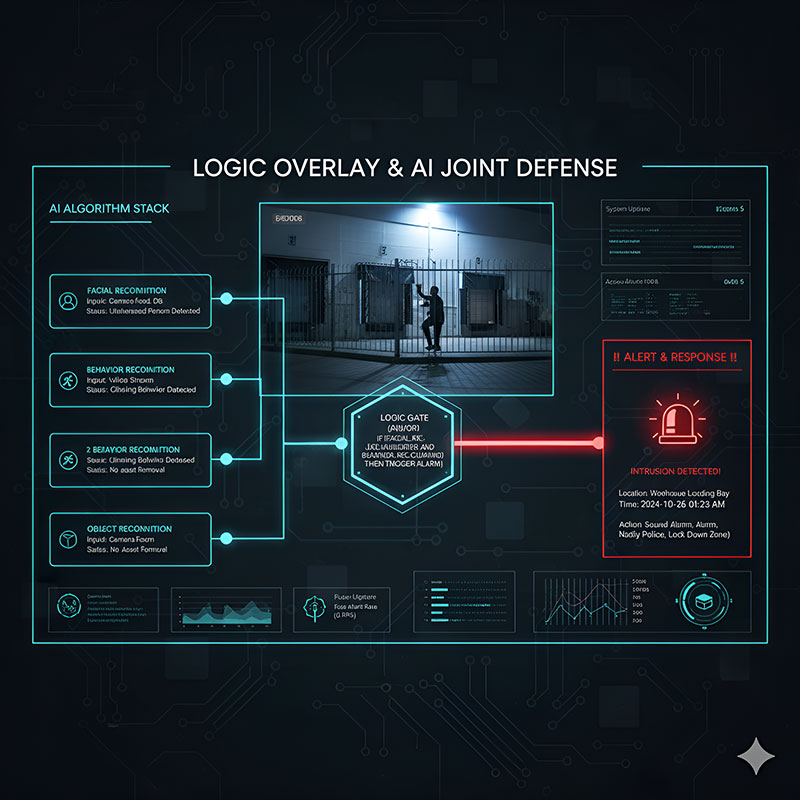
A major core advantage of this system is its powerful logic overlay capability. You can combine multiple recognition functions to form complex, high-precision alarm conditions, effectively reducing false alarms.
Example: You can set an "Intrusion Alarm" logic as: "If an unauthorized face (Facial Recognition) is detected within Area A (e.g., a warehouse entrance) AND climbing behavior (Behavior Recognition) is also detected, the alarm will be immediately triggered" after applying the AND or OR logic overlay.
This multi-factor verification mechanism ensures that only genuine security threats trigger an alert.
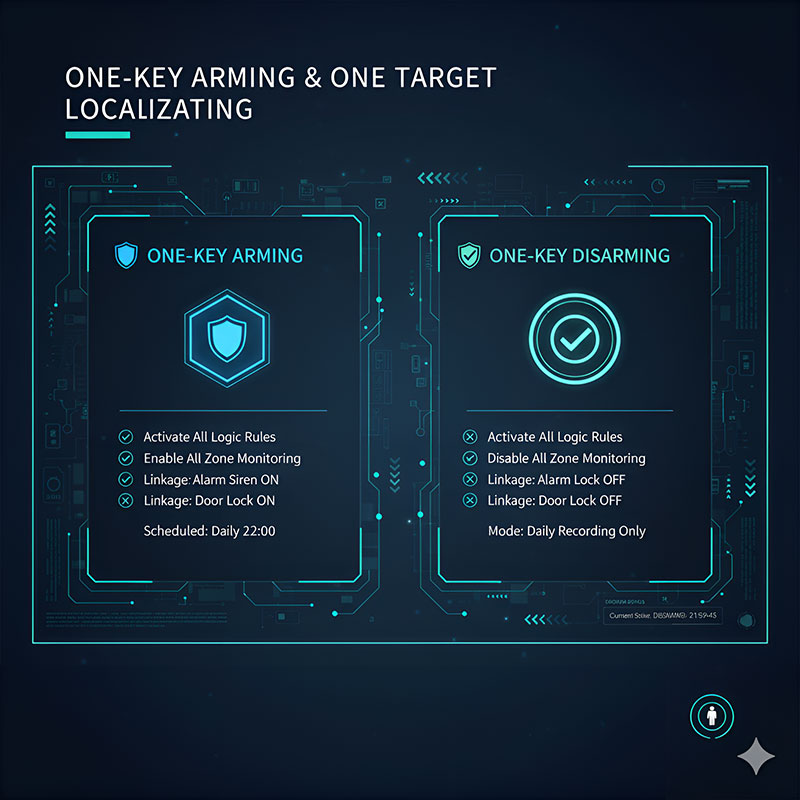
To ensure quick response and convenient daily management, the system offers one-key operation features:
One-Key Arming: Quickly activate all your preset alarm logics, area divisions, and linkage strategies. Suitable for high-alert periods such as after hours, nighttime, or holidays.
One-Key Disarming: Quickly deactivate all alarm logics, putting the system into routine monitoring mode (recording only, no alarming), which facilitates staff access and daily operations.
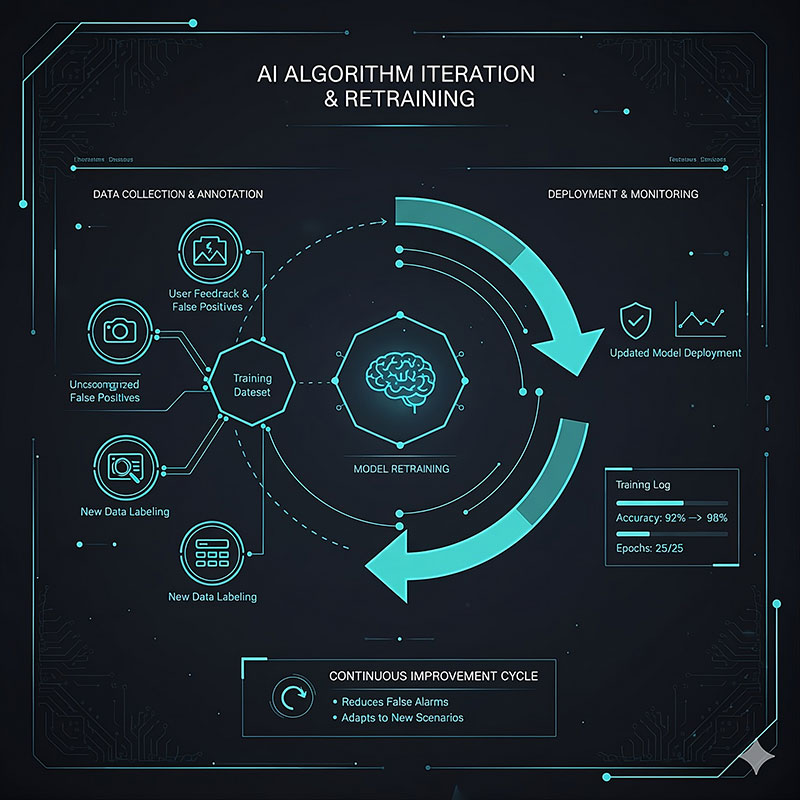
We understand that AI algorithms require continuous optimization to adapt to new business scenarios and environmental changes. Therefore this system supports Secondary Training (AI Algorithm Iteration):
During real-world operation, you can capture any misidentifications or missed detections. Simply reach out to our technical team, and we will use that data to retrain and refine the AI model for better performance.
This enables the algorithm to continuously self-improve and evolve, constantly increasing recognition accuracy and robustness in specific application scenarios, truly achieving the continuous iteration and long-term effective operation of the intelligent system.
Our AI customization algorithm service focuses on special scenarios and compliance requirements. Besides behavior recognition, face recognition, and basic object recognition, we are well aware that different industries have unique and highly demanding customization needs for monitoring analysis.
We provide a series of customized AI algorithm services targeting specific risks, safety, and compliance, aiming to fill the gap of general solutions and provide precise intelligent monitoring support for your special business scenarios. Such as smoking detection, smoke and fire detection, fire exit obstruction detection, hazardous materials detection, work uniform detection, and helmet detection.


Upgrading traditional monitoring to an intelligent perception brain, Achieving the transformation from passive recording to active early warning.